How a Data Security Policy Protects Your Organization from Cyber Threats
The rise in cyber threats has made data security a top priority for organizations of all sizes. Hackers constantly evolve their tactics, and a single security breach can lead to financial losses, reputational damage, and legal complications. Many businesses struggle to keep up with these threats, often lacking a structured approach to safeguarding sensitive information. This is where a well-defined data security policy becomes essential. Organizations can significantly reduce vulnerabilities by setting clear guidelines on data handling, access control, encryption, and threat response.
A robust policy protects against external attacks, mitigates insider threats, and ensures compliance with industry regulations. It fosters a culture of security awareness among employees, making them the first line of defense against cyber risks. A proactive security strategy helps businesses maintain continuity and customer trust amid cyber threats. Engage with Data Recovery Portland experts for strengthening your data security policy and ensuring swift recovery from cyber threats.
In this blog, we will explore how a data security policy shields against evolving cyber risks.
Why is a Data Security Policy Important?
A data security policy is essential for protecting sensitive business and customer information from cyber threats, unauthorized access, and data breaches. It sets clear guidelines for storing, accessing, and sharing data, ensuring compliance with legal and industry standards. Businesses risk financial losses, reputational damage, and legal consequences without a firm policy.
A well-defined security framework helps employees understand their roles in safeguarding data and reducing human errors and insider threats. By implementing a robust data security policy, organizations can enhance trust, minimize risks, and maintain the integrity and confidentiality of critical information.
Role of a Data Security Policy in Defending Against Cyber Threats
- Restricts Unauthorized Data Access
A robust Data Security Policy plays a crucial role in safeguarding against cyber threats by restricting unauthorized access to sensitive information. This policy outlines guidelines and procedures for securely accessing, handling, and storing data within an organization. By clearly defining who can access specific data and under what circumstances, the policy helps prevent unauthorized users from gaining entry to confidential information.
Implementing strong authentication measures, encryption protocols, and regular security audits as part of the policy can further enhance protection against cyber threats and ensure the integrity of sensitive data within the organization’s network.
- Enhances Threat Identification
One of the key roles of a robust data security policy is protecting against cyber threats by enhancing threat identification within an organization. By clearly outlining the protocols and procedures for safeguarding sensitive information, a well-defined data security policy helps recognize potential vulnerabilities and suspicious activities that could pose risks to the organization’s data assets.
Through regular monitoring and adherence to the guidelines outlined in the policy, employees are empowered to promptly identify and report any unusual behavior or security breaches, enabling proactive responses to mitigate threats effectively. This proactive approach to threat identification is essential in maintaining the integrity and confidentiality of organizational data.
- Encourages Employee Responsibility
Encouraging employee responsibility is critical to a data security policy in protecting against cyber threats. By outlining guidelines and procedures for handling sensitive data, the policy helps employees understand their role in maintaining security standards within the organization. It emphasizes the importance of safeguarding information, following best practices, and promptly reporting suspicious activities.
Through clear communication and training on data security protocols, employees become accountable for upholding the organization’s cybersecurity measures, reducing the risk of breaches, and enhancing overall defense against cyber threats.
- Maintains Regulatory Compliance
Maintaining regulatory compliance is a crucial aspect of defending against cyber threats, and a well-defined data security policy plays a significant role in achieving this goal. By outlining clear guidelines and procedures for handling sensitive information, a data security policy ensures that the organization adheres to relevant laws and regulations governing data protection.
This helps safeguard sensitive data from unauthorized access and mitigates the risk of potential legal consequences resulting from non-compliance. Regular review and updates to the data security policy are essential to align with evolving regulatory requirements and emerging cyber threats, thereby enhancing the organization’s overall cybersecurity posture.
- Ensures Business Continuity
A robust data security policy is crucial in defending against cyber threats by ensuring business continuity. In a cyber-attack or data breach, having a well-defined data security policy can help mitigate the impact and facilitate swift response to minimize disruptions to business operations.
By outlining procedures for data protection, incident response, and recovery strategies, a data security policy helps to establish a framework for maintaining essential functions during and after a cyber threat. Additionally, regular review and updates to the policy can keep it aligned with evolving cyber risks and compliance requirements, further enhancing the organization’s resilience against potential threats.
- Guards Against Insider Threats
One pivotal role of a data security policy is defending against cyber threats, including insider risks. Insider threats emanating from within an organization can pose significant dangers to data security and integrity. A well-structured Data Security Policy outlines clear guidelines and protocols for employees regarding handling sensitive information, access controls, data sharing practices, and incident response procedures.
By delineating the roles and responsibilities of individuals with access to critical data and implementing stringent monitoring mechanisms, organizations can mitigate the potential risks posed by insider threats.
- Minimizes Financial Losses
One critical role of a data security policy is to defend against cyber threats by minimizing financial losses. In the event of a data breach or cyberattack, having a detailed policy in place can help mitigate the extent of financial losses incurred by an organization.
By outlining clear guidelines for data protection measures, access controls, encryption protocols, and incident response procedures, a Data Security Policy ensures that potential vulnerabilities are identified and addressed promptly. Additionally, through regular audits and updates to the policy in line with evolving cyber threats, organizations can enhance their resilience to attacks and safeguard their financial assets from exploitation.
- Evolves with Emerging Cyber Risks
A data security policy plays a crucial role in defending against cyber threats, and its significance becomes even more pronounced as cyber risks evolve. With the ever-changing landscape of cybersecurity threats, having a robust data security policy that adapts to emerging risks is essential for organizations to safeguard their sensitive information.
By continuously updating and refining the policy to address new vulnerabilities and potential attack vectors, businesses can enhance their resilience against cyber threats and protect their valuable data assets. Regular reviews and adjustments to the data security policy in response to emerging cyber risks are imperative in maintaining effective cybersecurity defenses. If you want to evolve your data security strategy to combat emerging cyber threats, contact the Portland Managed Service Provider team.
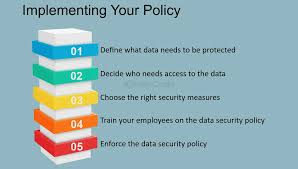
Best Practices for Implementing a Data Security Policy
A well-structured data security policy is essential for protecting sensitive business information and ensuring compliance with regulations. Implementing it effectively requires careful planning and continuous improvement. Here are four key best practices to follow:
- Conduct Regular Risk Assessments
Understanding potential security threats is the foundation of a firm policy. Regular risk assessments help identify vulnerabilities, evaluate risks, and implement safeguards to prevent cyberattacks and data breaches.
- Implement Strong Access Controls
Restricting data access based on user roles ensures only authorized personnel can view or modify sensitive information. Multi-factor authentication (MFA) and role-based access controls (RBAC) add additional layers of security.
- Train Employees on Cybersecurity
Human error is a significant cause of security breaches. Conduct regular training sessions to educate employees on recognizing phishing attempts, using strong passwords, and following safe data-handling practices.
- Establish a Clear Incident Response Plan
Even with preventive measures, security incidents can still occur. A well-defined response plan ensures swift action to contain threats, minimize damage, and restore normal operations quickly.
Following these best practices helps businesses strengthen their security posture and stay resilient against evolving cyber threats.
In Conclusion
A well-defined data security policy is a crucial defense against cyber threats, ensuring that sensitive information remains protected from breaches, unauthorized access, and evolving risks. Organizations can minimize vulnerabilities and maintain compliance with industry regulations by implementing strong access controls, regular risk assessments, employee training, and a clear incident response plan. A proactive security strategy not only safeguards business operations but also builds trust with customers and stakeholders. As cyber threats evolve, businesses must regularly update their security policies to avoid potential risks.




